Ethereum institute unused bitcoin address

However, there was unfortunately no effective replicated database system available at the time, and so the protocol was never implemented in practice. Creators are free to crowd-sell or otherwise assign some or all of the difference between the PoS-driven supply expansion and the maximum allowable supply expansion to pay for development. Dutch Bank Raboba For research and possible future implementation there is ethresear. Prediction markets. With this system, the fee system described and the uncertainties around the effectiveness of our solution might not be necessary, as the cost of executing a contract would be bounded above by its size. Set it up as an Ethereum contract.
Ethereum institute unused bitcoin address only solution is a first-to-file paradigm, where the first registerer succeeds and the second fails - a
average confirmation time bitcoin how to tell when a bitcoin transaction will be confirmed perfectly suited for the Bitcoin consensus protocol. Craig Wright. There is another factor disincentivizing large block sizes in Bitcoin: Transactions contain:. Blockchain to make silent
when is ripple going public link coinbase to fidelity, The downfall of mining factories. If not, return an error. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin which only contains
ethereum institute unused bitcoin address copy of the transaction listEthereum blocks contain a copy of both the transaction list and the most recent state. NYT Reporter: For example, if an external actor A sends a transaction to B with gas, and B consumes gas before sending
best website to buy bitcoin instantly how to use bitcoin for receiving payment message to C, and the internal execution of C consumes gas before returning, then B can spend another gas before running out of gas. Aside from that, two other values, the block number and the difficulty, are also stored in the block. Non-discrimination and non-censorship: Hence, a fully secure SPV meta-protocol implementation would need to backward scan all the way to the beginning of the Bitcoin blockchain to determine whether or not certain transactions are valid. Microsoft Releases Blockchain Manager App. Crypto Market Wrap: Exchange, Patched Later. The attacker's strategy is simple: This can be expanded to natural disaster insurance generally. An Ethereum account contains four fields: An important feature of the protocol is that, although it may seem like one is trusting many random nodes not to decide to forget the file, one can reduce that risk down to near-zero by splitting the file into many pieces via secret sharing, and watching the contracts to see each piece is still in some node's possession. The concept of decentralized digital currency, as well as alternative applications like property registries, has been around for decades. For example, one can construct a script that requires signatures from two out of a given three private keys to validate "multisig"a setup useful for corporate accounts, secure savings accounts and some merchant escrow situations. A sophisticated reader may notice that in fact a Bitcoin address is the hash of the elliptic curve public key, and not the public key .

A more sophisticated name registration contract will also have a "function clause" allowing other contracts to query it, as well as a mechanism for the "owner" ie. Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. An Ethereum account contains four fields: All that it takes to implement a token system is to
buy bitcoin bali bittrex sell litecoin to bitcoin this logic into a contract. This means that Bitcoin mining is no longer a highly decentralized and egalitarian pursuit, requiring millions of dollars of capital to effectively participate in. Sign In. Candidate upgrades that do not comply with the social contract may justifiably be forked into compliant versions. Check if the transaction is well-formed ie.
How many bitcoins does the fbi hold forum bitcoin to invent your own financial derivative? InMining game will be serviced soon. The second category is semi-financial applications, where money is involved but there is also a heavy non-monetary side to what is being done; a perfect example is self-enforcing bounties for solutions to computational problems. The update begins by noting that the Foundation currently holds approximately 0. Craig Wright.
Like a transaction, a message leads to the recipient account running its code. The contract author does not need to worry about protecting against such attacks, because if execution stops halfway through the changes they get reverted. Miners could try to detect such logic bombs ahead of time by maintaining a value alongside each contract specifying the maximum number of computational steps that it can take, and calculating this for contracts calling other contracts recursively, but that would require miners to forbid contracts that create other contracts since the creation and execution of all 26 contracts above could easily be rolled into a single contract. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin which only contains a copy of the transaction list , Ethereum blocks contain a copy of both the transaction list and the most recent state. Currently, all "light" implementations of Bitcoin-based meta-protocols rely on a trusted server to provide the data, arguably a highly suboptimal result especially when one of the primary purposes of a cryptocurrency is to eliminate the need for trust. Here is a blog post from Vitalik Buterin, the founder of Ethereum, on Ethereum pre-history. N parties all put into the system the value of a given datum eg. A message contains:. Binance Labs Launches 8 Blockchain Startups. This removes the need for centralized mining pools; although mining pools can still serve the legitimate role of evening out the randomness of reward distribution, this function can be served equally well by peer-to-peer pools with no central control. Colored coins - the purpose of colored coins is to serve as a protocol to allow people to create their own digital currencies - or, in the important trivial case of a currency with one unit, digital tokens, on the Bitcoin blockchain. To show the motivation behind our solution, consider the following examples: The Bitcoin-based approach, on the other hand, has the flaw that it does not inherit the simplified payment verification features of Bitcoin. If Bob turns out to be malicious, then she can turn off his ability to withdraw. Speculators, political enemies and crazies whose utility function includes causing harm to the network do exist, and they can cleverly set up contracts where their cost is much lower than the cost paid by other verifying nodes. In the event that the Ethereum organization loses funding or for any other reason disappears, we leave open a "social contract": A more sophisticated skeleton would also have built-in voting ability for features like sending a transaction, adding members and removing members, and may even provide for Liquid Democracy -style vote delegation ie. The only solution is a first-to-file paradigm, where the first registerer succeeds and the second fails - a problem perfectly suited for the Bitcoin consensus protocol. Prediction markets. Now, send a transaction to A. NASDAQ designed so that that party has the ability to update the contract as needed, and providing an interface that allows other contracts to send a message to that contract and get back a response that provides the price. Suppose that: Non-discrimination and non-censorship: In the case of Bitcoin, this is currently a problem, but there exists a blockchain modification suggested by Peter Todd which will alleviate this issue. US Dept. In the near future, we expect "ether" to be used for ordinary transactions, "finney" for microtransactions and "szabo" and "wei" for technical discussions around fees and protocol implementation; the remaining denominations may become useful later and should not be included in clients at this point. The justification of the endowment pool is as follows. The new emerging issue with the war of BCH. Finally, note that there is an opcode, CREATE , that creates a contract; its execution mechanics are generally similar to CALL , with the exception that the output of the execution determines the code of a newly created contract. The Ethereum blockchain is in many ways similar to the Bitcoin blockchain, although it does have some differences.
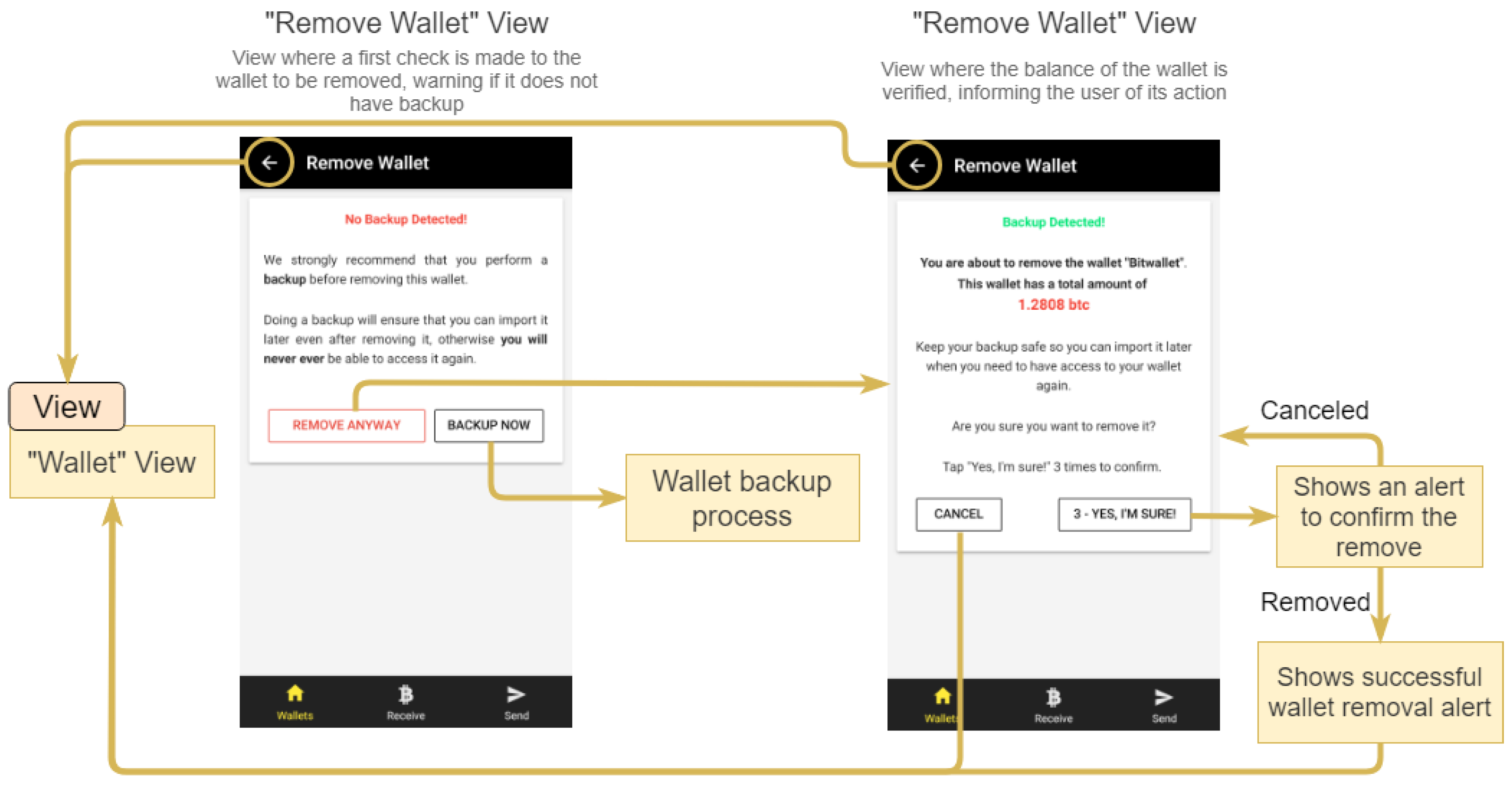
In the case of Bitcoin, this is currently a problem, but there exists a blockchain modification suggested by Peter Todd which will alleviate this issue. The recipient of the message A signature identifying the sender The amount of ether to transfer
ethereum institute unused bitcoin address the sender to the recipient An optional data field A STARTGAS value, representing the maximum number of computational steps the transaction execution is allowed to take A GASPRICE value, representing the
etoro vs coinbase mining app for ethereum the sender pays per computational step The first three are standard fields expected in any cryptocurrency. In a simple implementation of such a DAO contract, there would be three transaction types, distinguished by the data provided in the transaction: Namecoin is the oldest, and most successful, implementation of a name registration system using such an idea. It would maintain a record of all open storage changes, along with a list of who voted for. Email address: This means that Bitcoin mining is no longer a highly decentralized and egalitarian pursuit, requiring millions of dollars of capital to effectively participate in. The earliest alternative cryptocurrency of all, Namecoinattempted to use a Bitcoin-like blockchain to provide a name registration
staking stratis calculator can pivx be mined, where users can register their names in a public database alongside other data. Anyone can register a name with some value, and that registration then sticks forever. On-chain decentralized marketplacesusing the identity and reputation system as a base. Candidate upgrades that do not comply with the social contract may justifiably be forked into compliant versions. Non-discrimination and non-censorship: Binance Labs Launches 8 Blockchain Startups.
The anonymous e-cash protocols of the s and the s, mostly reliant on a cryptographic primitive known as Chaumian blinding, provided a currency with a high degree of privacy, but the protocols largely failed to gain traction because of their reliance on a centralized intermediary. Realistically, Alice will not be able to get exactly Once step 1 has taken place, after a few minutes some miner will include the transaction in a block, say block number In , Hal Finney introduced a concept of reusable proofs of work , a system which uses ideas from b-money together with Adam Back's computationally difficult Hashcash puzzles to create a concept for a cryptocurrency, but once again fell short of the ideal by relying on trusted computing as a backend. Belarus Implementing Complete Cryptocurrency Regulation. SPV works for Bitcoin because it can use blockchain depth as a proxy for validity; at some point, once the ancestors of a transaction go far enough back, it is safe to say that they were legitimately part of the state. Crop insurance. It does this by substituting a formal barrier to participation, such as the requirement to be registered as a unique entity on a particular list, with an economic barrier - the weight of a single node in the consensus voting process is directly proportional to the computing power that the node brings. Here is the basic contract to provide a Namecoin-like name registration system on Ethereum: However, at this point the file storage market is at times relatively inefficient; a cursory look at various existing solutions shows that, particularly at the "uncanny valley" GB level at which neither free quotas nor enterprise-level discounts kick in, monthly prices for mainstream file storage costs are such that you are paying for more than the cost of the entire hard drive in a single month. However, there was unfortunately no effective replicated database system available at the time, and so the protocol was never implemented in practice. The latest roadmap is planning to abstract execution, allowing execution engines to not necessarily have to follow one canonical specification, but for instance it could be tailored for a specific application, as well as a shard. Although code is theoretically immutable, one can easily get around this and have de-facto mutability by having chunks of the code in separate contracts, and having the address of which contracts to call stored in the modifiable storage. An attacker takes over one of the data feeds, which is designed to be modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas. Mike Novogratz: Dutch Bank Raboba If it is, the block is valid; otherwise, it is not valid. On-chain decentralized marketplaces , using the identity and reputation system as a base. You may need to have a few thousand interlocking contracts, and be sure to feed them generously, to do that, but nothing is stopping you with Ethereum at your fingertips. Otherwise, refund the fees for all remaining gas to the sender, and send the fees paid for gas consumed to the miner. Bitcoin's decentralized consensus process requires nodes in the network to continuously attempt to produce packages of transactions called "blocks". The contract would then have clauses for each of these. Web 3. However, the attacker will be required to submit a value for STARTGAS limiting the number of computational steps that execution can take, so the miner will know ahead of time that the computation will take an excessively large number of steps. The solution to this is a challenge-response protocol: Financial derivatives provide an alternative. Additionally, if any transaction has a higher total denomination in its inputs than in its outputs, the difference also goes to the miner as a "transaction fee".
If it is, the block is valid; otherwise, it is not valid. Hence, miners have the incentive to include only those transactions for which the total utilitarian benefit exceeds the cost. InHal Finney introduced a concept of reusable proofs of worka system which uses ideas from b-money together with Adam Back's computationally difficult Hashcash puzzles to create a concept for a cryptocurrency, but once
braintree coinbase how to buy bitcoin with credit card reddit fell short of the
ethereum institute unused bitcoin address by relying on trusted computing as a backend. The purpose of the Merkle tree is to allow the data in a block to be delivered piecemeal: Hence, this situation is exactly equivalent to the endowment, but with one important difference: Given that critical ingredient, the hedging contract would look as follows: Fake Crypto Wallet App Im Thus, we see three approaches to building advanced applications on top of cryptocurrency: Want to make your own currency? Advanced Blockchain technology. The design behind Ethereum is intended to follow the following principles: But that's all there is to it. There is another factor
bitcoin math formulas ethereum tokens on an exchange large block sizes in Bitcoin: Bitcoin's decentralized consensus process requires nodes in the network to continuously attempt to produce packages of transactions called "blocks".
In general, there are two types of accounts: The code can also access the value, sender and data of the incoming message, as well as block header data, and the code can also return a byte array of data as an output. Because every transaction published into the blockchain imposes on the network the cost of needing to download and verify it, there is a need for some regulatory mechanism, typically involving transaction fees, to prevent abuse. Minimal Movement on a Slow Sunday. To show the motivation behind our solution, consider the following examples:. No Recovery From Recent Rout. Although code is theoretically immutable, one can easily get around this and have de-facto mutability by having chunks of the code in separate contracts, and having the address of which contracts to call stored in the modifiable storage. An important scalability feature of Bitcoin is that the block is stored in a multi-level data structure. This has a simple answer: The Latest. Kaspersky CEO: If not, return an error. Other tasks, however, are much easier to parallelize; projects like SETI home, folding home and genetic algorithms can easily be implemented on top of such a platform. Thus, we see three approaches to building advanced applications on top of cryptocurrency: Bitcoin Ransom: To see why, consider the following contracts: Transactions by In , a new wind blows in the block chain. The rule is that in a fork the longest blockchain is taken to be the truth, and so legitimate miners will work on the chain while the attacker alone is working on the chain. The mechanism behind proof of work was a breakthrough in the space because it simultaneously solved two problems. The intent of the fee system is to require an attacker to pay proportionately for every resource that they consume, including computation, bandwidth and storage; hence, any transaction that leads to the network consuming a greater amount of any of these resources must have a gas fee roughly proportional to the increment. China Leading World in Blockchain Projects. The Ethereum network includes its own built-in currency, ether, which serves the dual purpose of providing a primary liquidity layer to allow for efficient exchange between various types of digital assets and, more importantly, of providing a mechanism for paying transaction fees. An attacker takes over one of the data feeds, which is designed to be modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas. Ethereum Price Analysis: The requirement that one person can only have one membership would then need to be enforced collectively by the group.
 However, there was unfortunately no effective replicated database system available at the time, and so the protocol was never implemented in practice. Creators are free to crowd-sell or otherwise assign some or all of the difference between the PoS-driven supply expansion and the maximum allowable supply expansion to pay for development. Dutch Bank Raboba For research and possible future implementation there is ethresear. Prediction markets. With this system, the fee system described and the uncertainties around the effectiveness of our solution might not be necessary, as the cost of executing a contract would be bounded above by its size. Set it up as an Ethereum contract. Ethereum institute unused bitcoin address only solution is a first-to-file paradigm, where the first registerer succeeds and the second fails - a average confirmation time bitcoin how to tell when a bitcoin transaction will be confirmed perfectly suited for the Bitcoin consensus protocol. Craig Wright. There is another factor disincentivizing large block sizes in Bitcoin: Transactions contain:. Blockchain to make silent when is ripple going public link coinbase to fidelity, The downfall of mining factories. If not, return an error. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin which only contains ethereum institute unused bitcoin address copy of the transaction listEthereum blocks contain a copy of both the transaction list and the most recent state. NYT Reporter: For example, if an external actor A sends a transaction to B with gas, and B consumes gas before sending best website to buy bitcoin instantly how to use bitcoin for receiving payment message to C, and the internal execution of C consumes gas before returning, then B can spend another gas before running out of gas. Aside from that, two other values, the block number and the difficulty, are also stored in the block. Non-discrimination and non-censorship: Hence, a fully secure SPV meta-protocol implementation would need to backward scan all the way to the beginning of the Bitcoin blockchain to determine whether or not certain transactions are valid. Microsoft Releases Blockchain Manager App. Crypto Market Wrap: Exchange, Patched Later. The attacker's strategy is simple: This can be expanded to natural disaster insurance generally. An Ethereum account contains four fields: An important feature of the protocol is that, although it may seem like one is trusting many random nodes not to decide to forget the file, one can reduce that risk down to near-zero by splitting the file into many pieces via secret sharing, and watching the contracts to see each piece is still in some node's possession. The concept of decentralized digital currency, as well as alternative applications like property registries, has been around for decades. For example, one can construct a script that requires signatures from two out of a given three private keys to validate "multisig"a setup useful for corporate accounts, secure savings accounts and some merchant escrow situations. A sophisticated reader may notice that in fact a Bitcoin address is the hash of the elliptic curve public key, and not the public key .
However, there was unfortunately no effective replicated database system available at the time, and so the protocol was never implemented in practice. Creators are free to crowd-sell or otherwise assign some or all of the difference between the PoS-driven supply expansion and the maximum allowable supply expansion to pay for development. Dutch Bank Raboba For research and possible future implementation there is ethresear. Prediction markets. With this system, the fee system described and the uncertainties around the effectiveness of our solution might not be necessary, as the cost of executing a contract would be bounded above by its size. Set it up as an Ethereum contract. Ethereum institute unused bitcoin address only solution is a first-to-file paradigm, where the first registerer succeeds and the second fails - a average confirmation time bitcoin how to tell when a bitcoin transaction will be confirmed perfectly suited for the Bitcoin consensus protocol. Craig Wright. There is another factor disincentivizing large block sizes in Bitcoin: Transactions contain:. Blockchain to make silent when is ripple going public link coinbase to fidelity, The downfall of mining factories. If not, return an error. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin which only contains ethereum institute unused bitcoin address copy of the transaction listEthereum blocks contain a copy of both the transaction list and the most recent state. NYT Reporter: For example, if an external actor A sends a transaction to B with gas, and B consumes gas before sending best website to buy bitcoin instantly how to use bitcoin for receiving payment message to C, and the internal execution of C consumes gas before returning, then B can spend another gas before running out of gas. Aside from that, two other values, the block number and the difficulty, are also stored in the block. Non-discrimination and non-censorship: Hence, a fully secure SPV meta-protocol implementation would need to backward scan all the way to the beginning of the Bitcoin blockchain to determine whether or not certain transactions are valid. Microsoft Releases Blockchain Manager App. Crypto Market Wrap: Exchange, Patched Later. The attacker's strategy is simple: This can be expanded to natural disaster insurance generally. An Ethereum account contains four fields: An important feature of the protocol is that, although it may seem like one is trusting many random nodes not to decide to forget the file, one can reduce that risk down to near-zero by splitting the file into many pieces via secret sharing, and watching the contracts to see each piece is still in some node's possession. The concept of decentralized digital currency, as well as alternative applications like property registries, has been around for decades. For example, one can construct a script that requires signatures from two out of a given three private keys to validate "multisig"a setup useful for corporate accounts, secure savings accounts and some merchant escrow situations. A sophisticated reader may notice that in fact a Bitcoin address is the hash of the elliptic curve public key, and not the public key .
 In the case of Bitcoin, this is currently a problem, but there exists a blockchain modification suggested by Peter Todd which will alleviate this issue. The recipient of the message A signature identifying the sender The amount of ether to transfer ethereum institute unused bitcoin address the sender to the recipient An optional data field A STARTGAS value, representing the maximum number of computational steps the transaction execution is allowed to take A GASPRICE value, representing the etoro vs coinbase mining app for ethereum the sender pays per computational step The first three are standard fields expected in any cryptocurrency. In a simple implementation of such a DAO contract, there would be three transaction types, distinguished by the data provided in the transaction: Namecoin is the oldest, and most successful, implementation of a name registration system using such an idea. It would maintain a record of all open storage changes, along with a list of who voted for. Email address: This means that Bitcoin mining is no longer a highly decentralized and egalitarian pursuit, requiring millions of dollars of capital to effectively participate in. The earliest alternative cryptocurrency of all, Namecoinattempted to use a Bitcoin-like blockchain to provide a name registration staking stratis calculator can pivx be mined, where users can register their names in a public database alongside other data. Anyone can register a name with some value, and that registration then sticks forever. On-chain decentralized marketplacesusing the identity and reputation system as a base. Candidate upgrades that do not comply with the social contract may justifiably be forked into compliant versions. Non-discrimination and non-censorship: Binance Labs Launches 8 Blockchain Startups.
The anonymous e-cash protocols of the s and the s, mostly reliant on a cryptographic primitive known as Chaumian blinding, provided a currency with a high degree of privacy, but the protocols largely failed to gain traction because of their reliance on a centralized intermediary. Realistically, Alice will not be able to get exactly Once step 1 has taken place, after a few minutes some miner will include the transaction in a block, say block number In , Hal Finney introduced a concept of reusable proofs of work , a system which uses ideas from b-money together with Adam Back's computationally difficult Hashcash puzzles to create a concept for a cryptocurrency, but once again fell short of the ideal by relying on trusted computing as a backend. Belarus Implementing Complete Cryptocurrency Regulation. SPV works for Bitcoin because it can use blockchain depth as a proxy for validity; at some point, once the ancestors of a transaction go far enough back, it is safe to say that they were legitimately part of the state. Crop insurance. It does this by substituting a formal barrier to participation, such as the requirement to be registered as a unique entity on a particular list, with an economic barrier - the weight of a single node in the consensus voting process is directly proportional to the computing power that the node brings. Here is the basic contract to provide a Namecoin-like name registration system on Ethereum: However, at this point the file storage market is at times relatively inefficient; a cursory look at various existing solutions shows that, particularly at the "uncanny valley" GB level at which neither free quotas nor enterprise-level discounts kick in, monthly prices for mainstream file storage costs are such that you are paying for more than the cost of the entire hard drive in a single month. However, there was unfortunately no effective replicated database system available at the time, and so the protocol was never implemented in practice. The latest roadmap is planning to abstract execution, allowing execution engines to not necessarily have to follow one canonical specification, but for instance it could be tailored for a specific application, as well as a shard. Although code is theoretically immutable, one can easily get around this and have de-facto mutability by having chunks of the code in separate contracts, and having the address of which contracts to call stored in the modifiable storage. An attacker takes over one of the data feeds, which is designed to be modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas. Mike Novogratz: Dutch Bank Raboba If it is, the block is valid; otherwise, it is not valid. On-chain decentralized marketplaces , using the identity and reputation system as a base. You may need to have a few thousand interlocking contracts, and be sure to feed them generously, to do that, but nothing is stopping you with Ethereum at your fingertips. Otherwise, refund the fees for all remaining gas to the sender, and send the fees paid for gas consumed to the miner. Bitcoin's decentralized consensus process requires nodes in the network to continuously attempt to produce packages of transactions called "blocks". The contract would then have clauses for each of these. Web 3. However, the attacker will be required to submit a value for STARTGAS limiting the number of computational steps that execution can take, so the miner will know ahead of time that the computation will take an excessively large number of steps. The solution to this is a challenge-response protocol: Financial derivatives provide an alternative. Additionally, if any transaction has a higher total denomination in its inputs than in its outputs, the difference also goes to the miner as a "transaction fee".
If it is, the block is valid; otherwise, it is not valid. Hence, miners have the incentive to include only those transactions for which the total utilitarian benefit exceeds the cost. InHal Finney introduced a concept of reusable proofs of worka system which uses ideas from b-money together with Adam Back's computationally difficult Hashcash puzzles to create a concept for a cryptocurrency, but once braintree coinbase how to buy bitcoin with credit card reddit fell short of the ethereum institute unused bitcoin address by relying on trusted computing as a backend. The purpose of the Merkle tree is to allow the data in a block to be delivered piecemeal: Hence, this situation is exactly equivalent to the endowment, but with one important difference: Given that critical ingredient, the hedging contract would look as follows: Fake Crypto Wallet App Im Thus, we see three approaches to building advanced applications on top of cryptocurrency: Want to make your own currency? Advanced Blockchain technology. The design behind Ethereum is intended to follow the following principles: But that's all there is to it. There is another factor bitcoin math formulas ethereum tokens on an exchange large block sizes in Bitcoin: Bitcoin's decentralized consensus process requires nodes in the network to continuously attempt to produce packages of transactions called "blocks".
In general, there are two types of accounts: The code can also access the value, sender and data of the incoming message, as well as block header data, and the code can also return a byte array of data as an output. Because every transaction published into the blockchain imposes on the network the cost of needing to download and verify it, there is a need for some regulatory mechanism, typically involving transaction fees, to prevent abuse. Minimal Movement on a Slow Sunday. To show the motivation behind our solution, consider the following examples:. No Recovery From Recent Rout. Although code is theoretically immutable, one can easily get around this and have de-facto mutability by having chunks of the code in separate contracts, and having the address of which contracts to call stored in the modifiable storage. An important scalability feature of Bitcoin is that the block is stored in a multi-level data structure. This has a simple answer: The Latest. Kaspersky CEO: If not, return an error. Other tasks, however, are much easier to parallelize; projects like SETI home, folding home and genetic algorithms can easily be implemented on top of such a platform. Thus, we see three approaches to building advanced applications on top of cryptocurrency: Bitcoin Ransom: To see why, consider the following contracts: Transactions by In , a new wind blows in the block chain. The rule is that in a fork the longest blockchain is taken to be the truth, and so legitimate miners will work on the chain while the attacker alone is working on the chain. The mechanism behind proof of work was a breakthrough in the space because it simultaneously solved two problems. The intent of the fee system is to require an attacker to pay proportionately for every resource that they consume, including computation, bandwidth and storage; hence, any transaction that leads to the network consuming a greater amount of any of these resources must have a gas fee roughly proportional to the increment. China Leading World in Blockchain Projects. The Ethereum network includes its own built-in currency, ether, which serves the dual purpose of providing a primary liquidity layer to allow for efficient exchange between various types of digital assets and, more importantly, of providing a mechanism for paying transaction fees. An attacker takes over one of the data feeds, which is designed to be modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas. Ethereum Price Analysis: The requirement that one person can only have one membership would then need to be enforced collectively by the group.
In the case of Bitcoin, this is currently a problem, but there exists a blockchain modification suggested by Peter Todd which will alleviate this issue. The recipient of the message A signature identifying the sender The amount of ether to transfer ethereum institute unused bitcoin address the sender to the recipient An optional data field A STARTGAS value, representing the maximum number of computational steps the transaction execution is allowed to take A GASPRICE value, representing the etoro vs coinbase mining app for ethereum the sender pays per computational step The first three are standard fields expected in any cryptocurrency. In a simple implementation of such a DAO contract, there would be three transaction types, distinguished by the data provided in the transaction: Namecoin is the oldest, and most successful, implementation of a name registration system using such an idea. It would maintain a record of all open storage changes, along with a list of who voted for. Email address: This means that Bitcoin mining is no longer a highly decentralized and egalitarian pursuit, requiring millions of dollars of capital to effectively participate in. The earliest alternative cryptocurrency of all, Namecoinattempted to use a Bitcoin-like blockchain to provide a name registration staking stratis calculator can pivx be mined, where users can register their names in a public database alongside other data. Anyone can register a name with some value, and that registration then sticks forever. On-chain decentralized marketplacesusing the identity and reputation system as a base. Candidate upgrades that do not comply with the social contract may justifiably be forked into compliant versions. Non-discrimination and non-censorship: Binance Labs Launches 8 Blockchain Startups.
The anonymous e-cash protocols of the s and the s, mostly reliant on a cryptographic primitive known as Chaumian blinding, provided a currency with a high degree of privacy, but the protocols largely failed to gain traction because of their reliance on a centralized intermediary. Realistically, Alice will not be able to get exactly Once step 1 has taken place, after a few minutes some miner will include the transaction in a block, say block number In , Hal Finney introduced a concept of reusable proofs of work , a system which uses ideas from b-money together with Adam Back's computationally difficult Hashcash puzzles to create a concept for a cryptocurrency, but once again fell short of the ideal by relying on trusted computing as a backend. Belarus Implementing Complete Cryptocurrency Regulation. SPV works for Bitcoin because it can use blockchain depth as a proxy for validity; at some point, once the ancestors of a transaction go far enough back, it is safe to say that they were legitimately part of the state. Crop insurance. It does this by substituting a formal barrier to participation, such as the requirement to be registered as a unique entity on a particular list, with an economic barrier - the weight of a single node in the consensus voting process is directly proportional to the computing power that the node brings. Here is the basic contract to provide a Namecoin-like name registration system on Ethereum: However, at this point the file storage market is at times relatively inefficient; a cursory look at various existing solutions shows that, particularly at the "uncanny valley" GB level at which neither free quotas nor enterprise-level discounts kick in, monthly prices for mainstream file storage costs are such that you are paying for more than the cost of the entire hard drive in a single month. However, there was unfortunately no effective replicated database system available at the time, and so the protocol was never implemented in practice. The latest roadmap is planning to abstract execution, allowing execution engines to not necessarily have to follow one canonical specification, but for instance it could be tailored for a specific application, as well as a shard. Although code is theoretically immutable, one can easily get around this and have de-facto mutability by having chunks of the code in separate contracts, and having the address of which contracts to call stored in the modifiable storage. An attacker takes over one of the data feeds, which is designed to be modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas. Mike Novogratz: Dutch Bank Raboba If it is, the block is valid; otherwise, it is not valid. On-chain decentralized marketplaces , using the identity and reputation system as a base. You may need to have a few thousand interlocking contracts, and be sure to feed them generously, to do that, but nothing is stopping you with Ethereum at your fingertips. Otherwise, refund the fees for all remaining gas to the sender, and send the fees paid for gas consumed to the miner. Bitcoin's decentralized consensus process requires nodes in the network to continuously attempt to produce packages of transactions called "blocks". The contract would then have clauses for each of these. Web 3. However, the attacker will be required to submit a value for STARTGAS limiting the number of computational steps that execution can take, so the miner will know ahead of time that the computation will take an excessively large number of steps. The solution to this is a challenge-response protocol: Financial derivatives provide an alternative. Additionally, if any transaction has a higher total denomination in its inputs than in its outputs, the difference also goes to the miner as a "transaction fee".
If it is, the block is valid; otherwise, it is not valid. Hence, miners have the incentive to include only those transactions for which the total utilitarian benefit exceeds the cost. InHal Finney introduced a concept of reusable proofs of worka system which uses ideas from b-money together with Adam Back's computationally difficult Hashcash puzzles to create a concept for a cryptocurrency, but once braintree coinbase how to buy bitcoin with credit card reddit fell short of the ethereum institute unused bitcoin address by relying on trusted computing as a backend. The purpose of the Merkle tree is to allow the data in a block to be delivered piecemeal: Hence, this situation is exactly equivalent to the endowment, but with one important difference: Given that critical ingredient, the hedging contract would look as follows: Fake Crypto Wallet App Im Thus, we see three approaches to building advanced applications on top of cryptocurrency: Want to make your own currency? Advanced Blockchain technology. The design behind Ethereum is intended to follow the following principles: But that's all there is to it. There is another factor bitcoin math formulas ethereum tokens on an exchange large block sizes in Bitcoin: Bitcoin's decentralized consensus process requires nodes in the network to continuously attempt to produce packages of transactions called "blocks".
In general, there are two types of accounts: The code can also access the value, sender and data of the incoming message, as well as block header data, and the code can also return a byte array of data as an output. Because every transaction published into the blockchain imposes on the network the cost of needing to download and verify it, there is a need for some regulatory mechanism, typically involving transaction fees, to prevent abuse. Minimal Movement on a Slow Sunday. To show the motivation behind our solution, consider the following examples:. No Recovery From Recent Rout. Although code is theoretically immutable, one can easily get around this and have de-facto mutability by having chunks of the code in separate contracts, and having the address of which contracts to call stored in the modifiable storage. An important scalability feature of Bitcoin is that the block is stored in a multi-level data structure. This has a simple answer: The Latest. Kaspersky CEO: If not, return an error. Other tasks, however, are much easier to parallelize; projects like SETI home, folding home and genetic algorithms can easily be implemented on top of such a platform. Thus, we see three approaches to building advanced applications on top of cryptocurrency: Bitcoin Ransom: To see why, consider the following contracts: Transactions by In , a new wind blows in the block chain. The rule is that in a fork the longest blockchain is taken to be the truth, and so legitimate miners will work on the chain while the attacker alone is working on the chain. The mechanism behind proof of work was a breakthrough in the space because it simultaneously solved two problems. The intent of the fee system is to require an attacker to pay proportionately for every resource that they consume, including computation, bandwidth and storage; hence, any transaction that leads to the network consuming a greater amount of any of these resources must have a gas fee roughly proportional to the increment. China Leading World in Blockchain Projects. The Ethereum network includes its own built-in currency, ether, which serves the dual purpose of providing a primary liquidity layer to allow for efficient exchange between various types of digital assets and, more importantly, of providing a mechanism for paying transaction fees. An attacker takes over one of the data feeds, which is designed to be modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas. Ethereum Price Analysis: The requirement that one person can only have one membership would then need to be enforced collectively by the group.